Tips for Practicing Safe Browsing on the Internet
A security breach is a nightmare for any company. Attackers are always trying to take advantage of every opportunity to get financial and identity information. Therefore, protection requires continuous due diligence on the company’s part. But the company is not the only one with responsibilities. There are responsibilities that your employees should have also. The…
Continue Reading Tips for Practicing Safe Browsing on the Internet
No, IT Support and Security are Not the Same
Most small to medium sized businesses intuitively know the difference between IT support and security. That doesn’t mean you address IT support and security separately when it comes to protecting your data and maintaining your infrastructure. Having both the necessary support to maintain your systems combined with adequate security to protect data is essential. Support…
Continue Reading No, IT Support and Security are Not the Same
What’s Slowing Down Your Device?
You rely on your device to get your work done. When your device is slow, your productivity level is affected. You have deadlines looming and risk going over budget if you can’t get the work done in a timely manner. But right now, all you can seem to do is stare at the screen, waiting…
The Benefits of System Performance Monitoring
Improving your system performance and increasing your productivity are goals every business wants to achieve. IT can be a big headache and cost you money when your system is slow or down. Therefore, system performance monitoring should be a priority against weaknesses and threats that are counterproductive and costly. 3 benefits of system performance monitoring…
Continue Reading The Benefits of System Performance Monitoring
Why Hackers Target Small Businesses: Unraveling the Cybersecurity Challenge
When it comes to computer security, your business data must be secure. As a small business, you can’t afford cyberattacks. Yet so much can happen. Employees can mistakenly open email spam or click on a malicious link while researching on the internet. Then there can be distributed denial of service (DDoS) attacks, like what happened…
Continue Reading Why Hackers Target Small Businesses: Unraveling the Cybersecurity Challenge
Tech Excellence: Navigating Atlanta Managed Services in Business Landscape
Atlanta-managed services have become the linchpin in the ever-evolving tech landscape. As businesses strive for excellence, the role of managed services in Atlanta has taken center stage, providing a robust framework for streamlined operations and unparalleled tech support. Understanding Atlanta Managed Services In the heart of the bustling business landscape, Atlanta managed services offer a…
Continue Reading Tech Excellence: Navigating Atlanta Managed Services in Business Landscape
Harnessing the Power of Managed Services in Your Business
In Atlanta’s dynamic and ever-evolving business landscape, companies increasingly recognize the strategic advantages of leveraging managed services atlanta. This comprehensive term, “managed services Atlanta,” encapsulates a diverse suite of outsourced solutions that have the potential to revolutionise. How businesses operate, manage their IT infrastructure, and adeptly navigate the complexities of the digital age. As organisations…
Continue Reading Harnessing the Power of Managed Services in Your Business
How the Right Managed Service Provider in Atlanta Can Make All the Difference
In the fast-paced world of business technology, finding the right managed service provider (MSP) is akin to discovering the perfect partner for a dance – seamless, reliable, and capable of keeping up with every twist and turn. For companies in Atlanta, having a trusted MSP by their side is not just an option; it’s a…
Continue Reading How the Right Managed Service Provider in Atlanta Can Make All the Difference
Invest in Growth: Superior IT Support Services in Atlanta, Georgia
Are you a business owner in Atlanta, Georgia, looking to propel your company to new heights? One crucial aspect is the quality of your IT support services. In today’s rapidly evolving digital landscape, having reliable IT support is not just a luxury; it’s a necessity. So, let’s delve into the IT support in Atlanta, Georgia…
Continue Reading Invest in Growth: Superior IT Support Services in Atlanta, Georgia
Keep Your Business Safe from Cyber Attacks – Hire the Best Cyber Security Company Now!
In today’s fast-paced digital landscape, where businesses thrive on interconnected networks and data-driven strategies, the need for a robust cyber security company has never been more critical. Cyber security companies play a pivotal role in safeguarding your business against the ever-evolving threats lurking online. As businesses become increasingly reliant on technology, the stakes are higher…
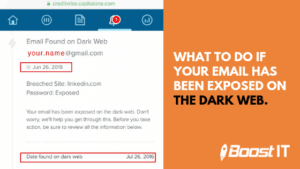
How to Check the Dark Web for Your Personal Information?
In the digital age, the protection of personal information, including knowing how to check the dark web for personal information, is more critical than ever. With the prevalence of cyber threats and data breaches, it’s essential to take proactive steps to ensure your data’s security. The “dark web” often harbors stolen personal information, making it…
Continue Reading How to Check the Dark Web for Your Personal Information?
17 New Cyber Liability Insurance Questions Your Provider Will Ask
In today’s digital age, where businesses heavily rely on technology, the threat of cyber attacks looms large. New Cyber Liability Insurance Questions have emerged as a crucial aspect of ensuring comprehensive protection against these evolving threats. To mitigate potential risks, many companies are turning to cyber liability insurance. This specialized coverage helps protect against the…
Continue Reading 17 New Cyber Liability Insurance Questions Your Provider Will Ask
Improving Efficiency and Achieving Success through Managed IT Services
Managed IT services offer numerous benefits for businesses, providing a proactive approach to IT management and support. By outsourcing their IT needs to a trusted managed service provider (MSP), companies can focus on their core operations while enjoying various advantages. Let’s explore the benefits of managed IT services in detail. Why Choose Managed IT Services…
Continue Reading Improving Efficiency and Achieving Success through Managed IT Services
Investing in Security: The Business Case for Hiring a Cybersecurity Company
The need for robust cybersecurity measures must be addressed in today’s hyper-connected digital landscape. Cybersecurity companies play a pivotal role in safeguarding organizations against the ever-evolving threats in the digital realm. Understanding the Cyber Threat Landscape The first step in recognizing the significance of a cybersecurity company lies in understanding the complex and dynamic nature…
Continue Reading Investing in Security: The Business Case for Hiring a Cybersecurity Company
Unlocking Business Potential: Atlanta Managed Services Best Practices
In the bustling business landscape of Atlanta, companies are constantly looking for ways to optimize their operations, streamline processes, and stay ahead of the competition. One key player in this game of business efficiency is managed services. If you’re a business owner in Atlanta, navigating the world of managed services can be the game-changer your…
Continue Reading Unlocking Business Potential: Atlanta Managed Services Best Practices
From Startup to Success: Atlanta IT Services for Growing Businesses
In the dynamic landscape of Atlanta’s business environment, startups, alongside the demand for Atlanta IT services, are emerging at a rapid pace. Navigating the challenges of the digital era requires robust IT services that can adapt and scale with the growth of your business. Whether you’re just starting or looking to elevate your operations, Atlanta…
Continue Reading From Startup to Success: Atlanta IT Services for Growing Businesses
Tech Excellence: Pioneering Managed Service Provider in Atlanta
In the heart of Atlanta, where the pace of business matches the city’s rhythm, one company stands out as a beacon of technological innovation and service excellence: a Managed Service Provider (MSP) that goes beyond the ordinary. When navigating the intricate landscape of technology support, businesses in Atlanta turn to this exceptional Managed Service Provider…
Continue Reading Tech Excellence: Pioneering Managed Service Provider in Atlanta
Elevate Your Business with Atlanta’s Managed IT Services Solutions
In the fast-paced business world, staying ahead requires more than ambition; it demands a strategic technological approach. And in Atlanta, where innovation and progress converge, the key to unlocking your business potential lies in leveraging the expertise of managed IT services. Unpacking the Power of Atlanta’s Managed IT Services Atlanta Managed IT Services are a…
Continue Reading Elevate Your Business with Atlanta’s Managed IT Services Solutions
Exploring the Extraordinary Services of Top Managed Services Providers
Modern businesses operate in a dynamic environment, and maintaining competitiveness calls for more than simply innovative goods and services—it also calls for a strong and flexible IT infrastructure. This is where Top Managed Services Providers (MSPs) step in, offering extraordinary services designed to optimize operations, enhance cybersecurity, and ensure business continuity. From proactive IT support…
Continue Reading Exploring the Extraordinary Services of Top Managed Services Providers
How a Cybersecurity Company Can Safeguard Your Business
Businesses depend increasingly on technology to improve productivity and streamline operations in today’s fast-paced digital environment. However, with these technological advancements comes a heightened risk of cyber threats that can jeopardize the very foundation of your business. It is where a cybersecurity company steps in, serving as a digital fortress to protect your valuable assets…
Continue Reading How a Cybersecurity Company Can Safeguard Your Business
Safeguarding Digital Frontiers: The Role of a Cyber Security Company
In an era of technological advancements, the digital realm has become integral to our lives. The internet has woven into our daily routines, from personal communications to business transactions. However, this increased connectivity has also created cyber threats that jeopardize our privacy, data integrity, and overall security. This is where the expertise of a proficient…
Continue Reading Safeguarding Digital Frontiers: The Role of a Cyber Security Company
7 Insane Ways Managed IT Companies Transform Businesses!
In the dynamic landscape of modern business, technological advancements have become the cornerstone of success. Amidst this digital revolution, Managed IT Companies have emerged as the unsung heroes, wielding transformative powers that revolutionize businesses in astonishing ways. From fortifying cybersecurity to optimizing operational efficiency, these IT wizards are reshaping industries. Here are seven insane ways…
Continue Reading 7 Insane Ways Managed IT Companies Transform Businesses!
Securing Your Business: 8 Essential Cybersecurity Tips
In today’s interconnected digital landscape, ensuring robust cybersecurity measures is paramount for safeguarding your business against malicious threats. The ever-evolving tactics of hackers demand proactive and comprehensive strategies to fortify your systems. To navigate this terrain effectively, here are eight invaluable tips curated to bolster your cybersecurity defenses and protect your sensitive data. Stay in…
Continue Reading Securing Your Business: 8 Essential Cybersecurity Tips
How Top Managed Services Providers Ensure Data Safety
In today’s digital landscape, where data is the lifeblood of businesses, ensuring its safety and security is paramount. Managed Services Providers (MSPs) play a crucial role in maintaining this valuable asset’s integrity, confidentiality, and availability. The question arises then: How do top-tier MSPs ensure client data safety? Understanding the Data Landscape Before delving into the…
Continue Reading How Top Managed Services Providers Ensure Data Safety
Navigating Cybersecurity: Atlanta IT Services Overview
Cybersecurity has become an indispensable concern for businesses, organizations, and individuals in the ever-evolving digital landscape. As technology advances, so do the complexities and vulnerabilities associated with it. Atlanta, known for its vibrant business community and tech ecosystem, stands at the forefront of addressing these challenges through various IT services and cybersecurity solutions. The Need…
Continue Reading Navigating Cybersecurity: Atlanta IT Services Overview
Atlanta Managed Service Providers: Streamlining Business Operations for Success
In the bustling hub of Atlanta, businesses of all sizes strive for excellence in their respective industries. To navigate the complexities of today’s digital landscape, many enterprises are turning to Managed Service Providers (MSPs) to streamline their operations, enhance efficiency, and ensure seamless technological integration. Understanding Managed Service Providers Managed Service Providers are specialized firms…
Continue Reading Atlanta Managed Service Providers: Streamlining Business Operations for Success
Navigating the Cutting Edge: Unveiling the Top Managed Services Providers
In today’s digital landscape, businesses rely heavily on robust technological infrastructures. Managed Services Providers (MSPs) have emerged as essential partners, offering services to streamline operations, fortify security, and drive innovation. Let’s delve into the realm of MSPs and explore the top players shaping the technological landscape. Understanding Managed Services Providers (MSPs) MSPs are third-party entities…
Continue Reading Navigating the Cutting Edge: Unveiling the Top Managed Services Providers
Atlanta’s Crucial Backbone: The Indispensable Role of IT Support
The significance of robust IT support services cannot be overstated in the bustling metropolis of Atlanta, Georgia. The city’s vibrant business landscape, burgeoning tech scene, and diverse enterprises underscore the crucial role of reliable and efficient IT infrastructure in driving success and maintaining operational continuity. From startups to established corporations, the demand for dependable IT…
Continue Reading Atlanta’s Crucial Backbone: The Indispensable Role of IT Support
Unveiling the Power of Managed Services in Atlanta for Business Success
In the bustling business landscape of Atlanta, managed services have emerged as a transformative force for companies striving to attain and sustain success. The rapid evolution of technology and the complexities of modern business operations have created a pressing need for efficient and reliable IT solutions. In this digital age, implementing managed services in Atlanta…
Continue Reading Unveiling the Power of Managed Services in Atlanta for Business Success
5 Myths about Managed IT Companies Debunked
In today’s fast-paced digital world, businesses of all sizes increasingly rely on managed IT companies to handle their technology needs. These companies provide a wide range of services, from network management to cybersecurity, making it easier for organizations to focus on their core operations. However, several misconceptions and myths surrounding managed IT companies can deter…
Continue Reading 5 Myths about Managed IT Companies Debunked
Role of Managed IT Services Companies in Business Success
Managed IT services companies are pivotal in today’s digital-centric business landscape. These companies offer various solutions to support organizations in their technological endeavors, ensuring efficiency, security, and streamlined operations. Below, we’ll explore the essential aspects of managed IT services companies, their benefits, and how to choose the right one for your business. What Are Managed…
Continue Reading Role of Managed IT Services Companies in Business Success
Atlanta IT Services – Empowering Businesses in the Digital Age
Technology is pivotal in ensuring efficiency, security, and growth in today’s rapidly evolving business landscape. Atlanta, a bustling hub of commerce and innovation, is no exception. The demand for reliable IT services in Atlanta has surged, with businesses of all sizes recognizing the need to stay competitive in the digital age. This article explores the…
Continue Reading Atlanta IT Services – Empowering Businesses in the Digital Age
Managed Services Providers List: Streamlining Your Business for Success
In today’s fast-paced digital landscape, businesses constantly seek efficient solutions to streamline their operations. Managed Services Providers (MSPs) have emerged as valuable partners, offering a range of IT services that cater to diverse business needs. In this article, we will explore the concept of managed services, delve into their significance, and provide a comprehensive list…
Continue Reading Managed Services Providers List: Streamlining Your Business for Success
IT Support Atlanta, Georgia: Keeping Businesses Running Smoothly
In today’s digital age, businesses in Atlanta, Georgia, rely heavily on their IT infrastructure to operate efficiently and effectively. Whether it’s a small startup or a large corporation, IT support plays a pivotal role in ensuring that all systems run smoothly. In this article, we’ll explore the world of IT support in Atlanta, discussing its…
Continue Reading IT Support Atlanta, Georgia: Keeping Businesses Running Smoothly
Unlocking Business Success with Managed IT Services
In today’s fast-paced digital world, businesses rely heavily on technology to stay competitive and relevant. The management of IT infrastructure is a critical component of any successful enterprise. In this article, we will explore the world of Managed IT Services, uncovering their benefits, the factors to consider when choosing a provider, and the future trends…
Continue Reading Unlocking Business Success with Managed IT Services
Atlanta Managed Services: Streamlining Your Business Operations
Staying ahead of the curve is essential in today’s competitive business environment. Atlanta Managed Services offers a solution enabling businesses to streamline operations, reduce costs, and access top-tier expertise. But what exactly are managed services, and how can they benefit your business? Let’s explore. What Are Managed Services? The Definition Managed services refer to outsourcing…
Continue Reading Atlanta Managed Services: Streamlining Your Business Operations
Managed IT Services: Your Solution for Business Efficiency
Technology is crucial in driving success and staying competitive in today’s fast-paced business world. Small or large companies rely on IT infrastructure for their daily operations. However, managing IT systems and services can be daunting, which is where Managed IT Services companies come into play. Managed IT Services Managed IT Services refer to outsourcing the…
Continue Reading Managed IT Services: Your Solution for Business Efficiency
Guardians of the Digital Realm: The Role of Cyber Security Company
In an era where digital threats loom large, the importance of cybersecurity cannot be overstated. With cyberattacks becoming increasingly sophisticated, organizations must fortify their defenses to safeguard sensitive data, maintain trust, and ensure business continuity. This article explores the pivotal role played by cybersecurity companies in this digital age, focusing on their significance and the…
Continue Reading Guardians of the Digital Realm: The Role of Cyber Security Company
Boosting Business Success: The Role of Managed IT Companies
In today’s fast-paced digital landscape, having a reliable and efficient IT infrastructure is crucial for businesses of all sizes. Managed IT companies play a pivotal role in ensuring that organizations can harness the power of technology to drive growth, enhance productivity, and stay competitive. In this comprehensive article, we will explore the world of managed…
Continue Reading Boosting Business Success: The Role of Managed IT Companies
Managed IT Atlanta: Navigating the World of Seamless IT Solutions
In today’s fast-paced business landscape, the role of technology has become paramount. Companies in Atlanta, Georgia, are no exception. Many businesses in the area are turning to managed IT services to stay competitive and ensure smooth operations. In this comprehensive guide, we will explore the world of managed IT in Atlanta, from its benefits to…
Continue Reading Managed IT Atlanta: Navigating the World of Seamless IT Solutions
Email Phishing Protection: Safeguarding Your Digital World
In today’s digital age, where communication is largely conducted through email, protecting yourself and your organization from email phishing attacks is paramount. Email phishing, a deceptive practice where cybercriminals impersonate trusted entities to trick individuals into revealing sensitive information, poses a significant threat to personal and professional security. In this comprehensive guide, we will delve…
Continue Reading Email Phishing Protection: Safeguarding Your Digital World
Cybersecurity Frameworks: Safeguarding the Digital Realm
In today’s hyperconnected world, where the digital landscape continues to evolve at an unprecedented pace, cybersecurity has become an integral part of our daily lives. From protecting sensitive personal information to securing critical infrastructure, the need for robust cybersecurity measures has never been greater. To address this growing concern, various cybersecurity frameworks have emerged as…
Continue Reading Cybersecurity Frameworks: Safeguarding the Digital Realm
IT Management Trends: Navigating the Digital Era
In today’s rapidly evolving digital landscape, effective IT management is paramount for businesses of all sizes. Keeping pace with the ever-changing technology landscape requires a proactive approach to IT management. In today’s digital age, information technology (IT) is the backbone of almost every organization. IT management has evolved significantly over the years to keep up…
Continue Reading IT Management Trends: Navigating the Digital Era
The Importance of Email Encryption: Safeguarding Your Digital Communications
In an era where digital communication plays a central role in both personal and professional spheres, ensuring the security and privacy of our emails has become paramount. Email encryption is a powerful tool that enables individuals and organizations to protect sensitive information, maintain confidentiality, and guard against cyber threats. In this article, we will delve…
Continue Reading The Importance of Email Encryption: Safeguarding Your Digital Communications
IT Consultation Services: Unlocking the Power of Expertise in a Tech-Driven Era
Ever wondered how businesses scale rapidly in a competitive tech landscape? The secret sauce often isn’t a ground-breaking product or a charismatic leader. Sometimes, it’s the power of informed decisions steered by IT consultation services. Let’s dive deep into the ocean of IT consultation, its importance, and how it shapes the modern business arena. What…
Continue Reading IT Consultation Services: Unlocking the Power of Expertise in a Tech-Driven Era
Demystifying the World of Cybersecurity Consulting: A Comprehensive Guide
Ever heard the phrase, “It’s not about if you’ll be hacked, but when”? In our increasingly digital age, this statement rings truer than ever. The Role of Cybersecurity Consultants revolves around assisting companies in strengthening their cyber defense mechanisms. They use their specialized skills to identify vulnerabilities and create strategies to mitigate them. Wondering Why…
Continue Reading Demystifying the World of Cybersecurity Consulting: A Comprehensive Guide
IT Management Benefits: A Guide to Maximizing Efficiency and Productivity
In today’s technology-driven world, efficient IT management is crucial for businesses of all sizes. From streamlining operations to enhancing cybersecurity, effective IT management can offer a plethora of benefits that contribute to the overall success of an organization. In this article, we will explore the numerous advantages of IT management and how it can propel…
Continue Reading IT Management Benefits: A Guide to Maximizing Efficiency and Productivity
Email Communication Security: Safeguarding Your Digital Conversations
In the fast-paced digital era we live in today, email communication has become an integral part of our personal and professional lives. It’s our go-to medium for sharing information, conducting business transactions, and staying connected with friends and colleagues. However, as the reliance on email continues to grow, so does the need for robust email…
Continue Reading Email Communication Security: Safeguarding Your Digital Conversations
Expert IT Consultation: Navigating the Digital Landscape with Confidence
In today’s rapidly evolving digital landscape, businesses of all sizes face a common challenge: keeping up with the ever-changing world of technology. From optimizing their online presence to ensuring data security and streamlining IT operations, organizations require expert guidance to navigate the complex IT terrain successfully. In this comprehensive guide, we will explore the significance…
Continue Reading Expert IT Consultation: Navigating the Digital Landscape with Confidence
Cyber Threat Prevention: Safeguarding Your Digital World
In an increasingly interconnected digital landscape, cyber threats loom large. Cybercriminals are continually devising new methods to breach security systems, compromise sensitive data, and disrupt the normal flow of digital operations. To protect yourself, your business, and your online presence, it’s crucial to understand cyber threat prevention strategies. Understanding Cyber Threats Before diving into preventive…
Continue Reading Cyber Threat Prevention: Safeguarding Your Digital World
IT Management Strategies: Navigating the Digital Landscape
In today’s fast-paced and technology-driven world, effective IT management strategies have become essential for businesses to remain competitive and thrive. With the rapid advancements in digital technology, companies need to adopt comprehensive approaches to manage their IT resources and operations. In this article, we will delve into the key IT management strategies that can empower…
Continue Reading IT Management Strategies: Navigating the Digital Landscape
Microsoft Office 365 Integration: Streamlining Your Workflow
In today’s fast-paced digital world, seamless communication and efficient collaboration are crucial for businesses to thrive. Microsoft Office 365, a comprehensive suite of productivity tools, has become a staple for organizations seeking to enhance their operations. This article explores the ins and outs of Microsoft Office 365 integration, highlighting its benefits, challenges, and best practices.…
Continue Reading Microsoft Office 365 Integration: Streamlining Your Workflow
Effective IT Consultation: Navigating the Path to Technological Success
In today’s rapidly evolving business landscape, harnessing the power of technology is no longer a choice but a necessity. To ensure seamless integration and optimal utilization of technological solutions, organizations often turn to IT consultation services. Effective IT consultation can be the cornerstone of a successful digital transformation journey. In this article, we will delve…
Continue Reading Effective IT Consultation: Navigating the Path to Technological Success
Cybersecurity Measures: Safeguarding Your Digital World
In today’s interconnected world, where data breaches and cyber threats are on the rise, implementing robust cybersecurity measures is essential to protect sensitive information and maintain digital trust. This article explores various cybersecurity measures that individuals and organizations can adopt to safeguard their digital assets from cybercriminals. Understanding Cybersecurity Defining Cybersecurity Cybersecurity involves a set…
Continue Reading Cybersecurity Measures: Safeguarding Your Digital World
IT Management Best Practices: Navigating the Digital Landscape
In today’s fast-paced digital era, effective IT management plays a pivotal role in ensuring smooth business operations, improving customer experiences, and driving growth. As organizations of all sizes and industries rely heavily on technology, it’s crucial to adopt the right IT management practices to stay competitive and resilient. In this article, we will explore a…
Continue Reading IT Management Best Practices: Navigating the Digital Landscape
The Power of Efficiency: Unveiling the Benefits of a Managed IT Services Firm
In the dynamic landscape of technology, businesses are challenged to not only stay competitive but also maintain their digital infrastructure effectively. This is where Managed IT Services Firms step in, offering a comprehensive solution to streamline operations and enhance productivity. In this blog, we’ll delve into the world of managed IT services firms, exploring their…
Continue Reading The Power of Efficiency: Unveiling the Benefits of a Managed IT Services Firm
Managed IT Services Atlanta: Streamlining Your Business for Success
In today’s fast-paced digital landscape, businesses in Atlanta are recognizing the paramount importance of efficient and effective IT management. Managed IT services have emerged as a game-changer for companies of all sizes, offering them a comprehensive solution to streamline their technological infrastructure, enhance security, and boost overall operational efficiency. Let’s delve into the world of…
Continue Reading Managed IT Services Atlanta: Streamlining Your Business for Success
Navigating the Benefits of IT Managed Services: Your Ultimate Guide
If you’ve ever found yourself in a tech-related predicament – from network glitches to software crashes – you understand the value of efficient IT support. However, finding the right IT services nearby can be a daunting task. That’s where IT-managed services come into play. In this comprehensive guide, we’ll explore the benefits of IT-managed services,…
Continue Reading Navigating the Benefits of IT Managed Services: Your Ultimate Guide
Unlocking Efficient IT Services in Atlanta: Your Gateway to Seamless Tech Solutions
In today’s fast-paced business landscape, technology is the backbone of success. From startups to established enterprises, businesses in Atlanta are embracing IT services to streamline their operations, enhance cybersecurity, and foster growth. In this comprehensive guide, we will delve into the realm of IT services in Atlanta, exploring a spectrum of solutions that cater to…
Continue Reading Unlocking Efficient IT Services in Atlanta: Your Gateway to Seamless Tech Solutions
Navigating the Landscape: Your Ultimate Guide to Managed Services Providers List
In today’s rapidly evolving digital landscape, businesses are increasingly relying on technology to drive growth, efficiency, and innovation. However, managing complex IT systems can be challenging and resource-intensive. This is where Managed Services Providers (MSPs) step in, offering expert IT support and solutions tailored to meet the unique needs of businesses. In this comprehensive guide,…
Continue Reading Navigating the Landscape: Your Ultimate Guide to Managed Services Providers List
Redefining IT Support: Unveiling the Top Managed Service Providers
Managed service providers play a pivotal role in today’s fast-paced business landscape. In this article, we’ll explore the world of managed services and highlight the top providers in the industry. From IT infrastructure management to cybersecurity and cloud solutions, we’ll delve into the criteria for evaluating these providers and the benefits of partnering with the…
Continue Reading Redefining IT Support: Unveiling the Top Managed Service Providers
Choosing the Best Local IT Service Provider: A Comprehensive Guide
Finding the right IT service provider nearby can be a game-changer for your business. With several options available, it’s crucial to assess their offerings and expertise. Here’s a comprehensive guide to help you make an informed decision. Understanding the Need for IT Services in Your Locality The role of IT services extends beyond fixing technical…
Continue Reading Choosing the Best Local IT Service Provider: A Comprehensive Guide
Exploring the Benefits of Local Managed Service Providers
MSPs are IT experts who offer proactive management and support services to businesses. Local Managed Service Providers bring several benefits to the table, making them a valuable asset for organizations. Cost-Effective Solutions Local MSPs offer cost-effective IT solutions compared to establishing and maintaining an in-house IT department. Businesses can avoid the expenses associated with hiring…
Continue Reading Exploring the Benefits of Local Managed Service Providers
Understanding the Role of IT-Managed Service Providers in Business Success
Businesses of all sizes and industries are increasingly turning to IT-managed service providers to handle their IT needs efficiently. An IT managed service provider (MSP) is a third-party company that takes care of a client’s IT infrastructure, offering a proactive and strategic approach to managing and supporting IT systems. MSPs help businesses focus on their…
Continue Reading Understanding the Role of IT-Managed Service Providers in Business Success
Managed Service Atlanta: Empowering Businesses with Efficient IT Solutions
In today’s fast-paced digital landscape, businesses in Atlanta face increasing challenges managing their IT infrastructure effectively. To stay competitive and focus on their core operations, many companies turn to managed service providers for comprehensive IT solutions. In this article, we will delve into the world of managed services in Atlanta, exploring the benefits they offer,…
Continue Reading Managed Service Atlanta: Empowering Businesses with Efficient IT Solutions
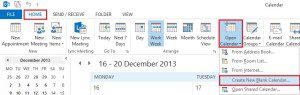
How To Create a Shared Calendar in Outlook 2021 & Microsoft 365?
If you would like to create a separate calendar in Exchange you need to use Microsoft Outlook 2021. Other users that want to view your new shared calendar will need to use Microsoft Outlook 2021 or the Outlook Web App in Microsoft 365.Scroll down or click each version to go directly to those instructions. Outlook…
Continue Reading How To Create a Shared Calendar in Outlook 2021 & Microsoft 365?
How To Create A Shared Calendar
Staying organized and managing schedules efficiently is essential in today’s fast-paced world. One effective way to achieve this is by using a shared calendar. A shared calendar allows multiple individuals or teams to access, collaborate, and stay updated on important events and appointments. In this topic, we will survey the benefits of using a shared…
Boosting Business Efficiency with IT Support in Atlanta, Georgia
Technology is crucial in enhancing productivity and efficiency in today’s fast-paced business world. One of the critical components of a successful business is having reliable IT support. In Atlanta, Georgia, companies increasingly recognize the importance of IT support services in streamlining their operations and staying ahead of the competition. This article explores how IT support…
Continue Reading Boosting Business Efficiency with IT Support in Atlanta, Georgia
Why Programs Won’t Open on Windows 7 and How to Fix It?
Having programs that will open on your Windows 7 computer can be frustrating and help productivity. This article aims to explore the possible causes behind this issue and provide you with practical solutions to resolve it. We will discuss why programs won’t open on Windows 7, the potential reasons behind this problem, and various methods…
Continue Reading Why Programs Won’t Open on Windows 7 and How to Fix It?
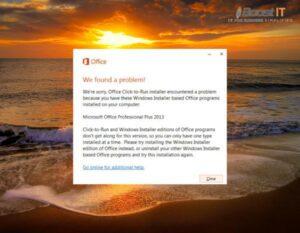
Microsoft Office Click-to-Run In Windows 10 – Tips & Best Practices
Microsoft Office Click-to-Run is a popular installation technology used by Microsoft for deploying and updating the Microsoft Office suite. It provides users with a convenient and efficient way to install and manage their Office applications. In this article, we will explore what Microsoft Office Click-to-Run is, how to get started with it, and share some…
Continue Reading Microsoft Office Click-to-Run In Windows 10 – Tips & Best Practices
Microsoft Office Won’t Open? Here’s What You Can Do
Having trouble with Microsoft Office not opening can be frustrating, especially when you have important tasks to complete.Whether it’s Microsoft Word, Excel, PowerPoint, or any other Office application, encountering issues with opening them can hinder your productivity.In this article, we’ll explore common reasons for Microsoft Office not opening and provide troubleshooting steps to help you…
Continue Reading Microsoft Office Won’t Open? Here’s What You Can Do
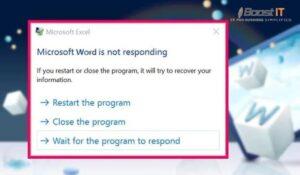
Why Is Microsoft Word Not Responding On Windows 10 Or Mac?
Microsoft Word is a widely used word-processing application that sometimes encounters issues where it becomes unresponsive or freezes. This can be frustrating, especially when you’re in the middle of an important document. This article will explore the common causes of Microsoft Word not responding to errors and provide practical solutions to resolve the issue on…
Continue Reading Why Is Microsoft Word Not Responding On Windows 10 Or Mac?
Cybersecurity Vs. Information Security – What You Need To Know
In today’s digital age, protecting sensitive data and information is paramount. “cybersecurity” and “information security” are often used interchangeably, but they have distinct differences. This article will provide the following: A comprehensive overview of cybersecurity and information security. Highlighting their essential components and differences. Similarities. The collaboration between the two. So let’s dive in and…
Continue Reading Cybersecurity Vs. Information Security – What You Need To Know
The Ultimate Guide To Running Diagnostics On Windows 10
When it comes to troubleshooting and maintaining the health of your Windows 10 system, running diagnostics is an essential practice. Diagnostics help identify and resolve issues, ensuring your computer runs smoothly. In this guide, we will explore the various aspects of running diagnostics on Windows 10, including the reasons to do so, understanding the diagnostics…
Continue Reading The Ultimate Guide To Running Diagnostics On Windows 10
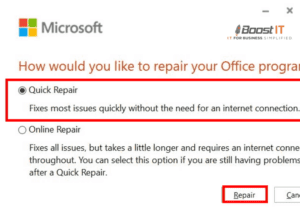
Microsoft Office Repair 101 – Fixing Your Productivity Suite
Microsoft Office is a widely used suite of productivity applications that includes programs like Word, Excel, PowerPoint, and Outlook. However, like any software, Microsoft Office can encounter issues that hinder its functionality. This article will explore common problems with Microsoft Office, troubleshooting techniques for repairs, and preventive measures for a smooth user experience. Common Issues…
Continue Reading Microsoft Office Repair 101 – Fixing Your Productivity Suite
How To Reboot Windows 10? – Quick Ways To Restart Your PC
Windows 10 is a powerful operating system that requires occasional reboots to maintain optimal performance. If you’re wondering how to reboot your Windows 10 computer, you’re in the right place. In this article, we’ll explore various methods to restart your PC easily and efficiently. Reasons To Reboot Windows 10 Before we delve into the different…
Continue Reading How To Reboot Windows 10? – Quick Ways To Restart Your PC
Microsoft Word Not Opening? Here’s How To Troubleshoot
Are you facing issues with Microsoft Word not opening on your computer? It can be frustrating when you need help accessing important documents or starting a new project. However, there are various reasons why Microsoft Word may not open, and several troubleshooting steps you can take to resolve the issue. In this article, we’ll explore…
Continue Reading Microsoft Word Not Opening? Here’s How To Troubleshoot
Cybersecurity Compliance – Stay Ahead Of Evolving Threats!
The cybersecurity scenery is constantly evolving, with new threats emerging every day. Organizations must prioritize cybersecurity compliance to safeguard sensitive data and protect against cyberattacks. By adhering to established standards and regulations, businesses can ensure that their security practices align with industry best practices and legal requirements. What Is Cybersecurity Compliance? Cybersecurity compliance refers to…
Continue Reading Cybersecurity Compliance – Stay Ahead Of Evolving Threats!
11 Ways To Fix Programs That Won’t Open On Windows 10
Have you encountered the frustrating issue of programs not opening on your Windows 10 computer? It can be incredibly inconvenient and hinder your productivity. This comprehensive troubleshooting guide will explore common causes behind this problem and provide practical solutions to resolve it. So, let’s dive in and get your programs running smoothly again! Common Causes…
Continue Reading 11 Ways To Fix Programs That Won’t Open On Windows 10
How To Choose a New Laptop
If you want to know how to choose a new laptop, you’ve come to right place. Choosing a laptop can be a really frustrating process. Even if you know some of what you want, choosing the hardware specs, model, manufacturer, finding one and then getting a good price can be a daunting process. And you want…
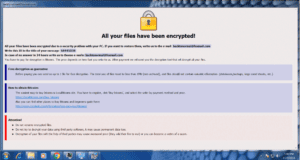
Atlanta Real Estate Firm Gets Ransomware
A Story about Ransomware Detection and Prevention for an Atlanta Real Estate Firm This is the story of how cyber criminals in China attempted to take down and extort for ransom an Atlanta Real Estate Firm, how the Boost IT team reacted, and what we can learn from it — ransomware prevention in 2020. How…
Cloud File Sync and Share Provides Speed and Efficiency
Real estate companies are learning the benefits of cloud file sync and share technology to simplify the way they create and share data and collaborate with their team and clients. You can upload files with a click from any device and access them at any time. Share a property survey with a potential buyer or…
Continue Reading Cloud File Sync and Share Provides Speed and Efficiency
How the Cloud is Helping Engineering
There are 4 ways the cloud is helping engineering. Cloud computing has changed how engineering and other industries are bidding for and completing projects. The cloud is secure, fast, reliable and full-featured – perfect for engineers to be productive and competitive. So, how are engineers using the cloud? It helps engineering keep things moving When designing…
Identifying Gaps in Your Cybersecurity
Many businesses recognize that cybersecurity is a growing threat and they prioritize it. They update software regularly, maintain their infrastructure and implement security measures to help thwart malicious attacks. They set up password protection access to computers, software, and apps so only those authorized can get access. They have their employees regularly change passwords. But…
How to Prevent Ransomware
Do you know the one I.T. question you should be asking? This question is directed at you. Whether you are an individual trying to secure your digital footprint or an employee /owner working for a business, do you know the one I.T. question you should be asking? We do, and we want you to know…
Streamline Your Business with the Cloud
When you streamline your business with the cloud, there is no more need to build out and maintain a complex IT infrastructure. Your operations become more agile and you can reduce costs. Cloud computing helps in streamlining your business so your employees can improve productivity and be more competitive. With quick access to the cloud,…
FTC Proposes adding Detailed Cybersecurity Requirements to Safeguards Rule
On March 5, 2019 the Federal Trade Commission (“FTC”) published requests for comment on proposed amendments to two key rules under the Gramm-Leach-Bliley Act (“GLBA”). Most significantly, the FTC proposes to add more detailed cybersecurity requirements to the Safeguards Rule. The rule governs the information security programs financial institutions must implement to protect customer data.…
Continue Reading FTC Proposes adding Detailed Cybersecurity Requirements to Safeguards Rule
How to Create a Strong Password
Follow these 4 tips to secure your online accounts Knowing how to create a strong password can help prevent fraud and unauthorized access to your personal and financial information. But what is a strong password? Check out the tips below. 1. Create Long, Complex Passwords Shorter passwords may be easier to remember, but they usually…
Turn On Do Not Disturb in Mac OS X
So I was in a video screenshare meeting yesterday and the person I met with needed to know how to Turn On Do Not Disturb in Mac OS X. Ever get those annoying notifications on your Mac while you’re in a public place, presentation, screenshare, or video meeting? Me too, but it’s easy to turn…
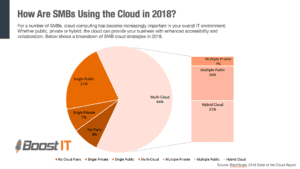
How Are SMBs Using the Cloud in 2018? [CHART]
So How are SMBs using the Cloud? It’s not just a buzzword. Read on to find out how using the cloud can cut costs and increase revenue through efficiency. This year has ushered in many technological changes, most notably the adoption in the small- and medium-sized business (SMB) of things like mobile and cloud solutions.…
Continue Reading How Are SMBs Using the Cloud in 2018? [CHART]
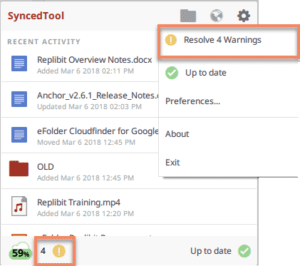
How to Resolve a File Sync Warning
How to resolve a file sync warning on a Windows or Mac machine: When an issue occurs, you will see a Resolve Sync Warning icon over the following (your icon may look like a rocket): System tray icon: System tray menu: Affected file: Click the icon on your computer’s system tray or menu bar, and select…
5 Time-Saving Tech Tips
When it comes to saving time at work, we all want the best tech tips so we can be more productive. Better tech is not always the answer to your everyday productivity problems. Sometimes it can seem like we are spending more time on devices, even though we have the best. While technology is continuously…
How to share contacts in Outlook 2016 and Office 365?
How to share contacts in Outlook 2016 and Office 365 with specific people in your organization Knowing how to share contacts in Outlook 2016 and Office 365 can be a huge timesaver for companies of any size. The default Contacts folder in Outlook is created in each Outlook profile. This folder can’t be renamed or…
Continue Reading How to share contacts in Outlook 2016 and Office 365?
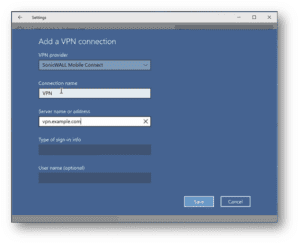
How to install SonicWall Mobile Connect on Windows 10?
How to install SonicWall Mobile Connect on Windows 10 Description This article explains how to install SonicWall Mobile Connect for Windows 10. Mobile Connect is the recommended VPN Client for Windows 10. Cause Resolution SonicWall Mobile Connect for Windows 10 is installed from the Microsoft Store. 1.On your Windows 10 device, launch the Store app.…
Continue Reading How to install SonicWall Mobile Connect on Windows 10?
The Scenario of the Infected Computer
The whole infected computer problem started when a coworker was sharing a computer to review a document and get other help. Before they realized what was going on, a pop-up window came up notifying them that you have an infected computer and suggested running a scan. The employees ran the scan but nothing happened. Everything…
Using Technology as a Game Changer
At Boost IT, we hold quarterly business meetings with our clients to maximize their success through the use of technology. During one quarterly business meeting with an engineering client, the owner mentioned a productivity concern. The concern was that his most productive engineers needed the fastest technology. In response, we configured his machines to make…
Do You Know Where Your IT is Vulnerable?
You might know a few people who avoid social media because they feel their personal identity will be compromised. You might also know a few people who are hesitant to use online banking for this same reason. Most of these people have no idea how many of their devices are connected to the internet and…
IT Recovery After a Major Flood
Natural disasters can be devastating. A major flood can destroy everything. When we look at the flooding from Hurricane Harvey, it can be difficult to imagine that it can happen to any of us. But it can. While a business can rebuild and purchase new IT infrastructure, what would happen to your business in the…
Cloud Storage vs Dedicated Servers
Have you heard other SMBs talk about their migration to the cloud? You might be thinking about ditching your dedicated server and using cloud storage. But is it right for you? Before you decide between cloud storage versus a dedicated server, recognize that you are probably already using cloud storage. If you store photos in…