The healthcare industry is a great example of how we see technology changing the way big data can be managed to benefit everyone. Big data is a term that describes data sets, or the large volume of data, that we use everyday but which are so complex that traditional data processing application software is inadequate to deal with them. During the last decade, we have seen huge advancements in how we use technology to generate, store, and analyze big data. Technology has helped the healthcare industry become more efficient and productive.
Using Big Data for Healthcare Prevention
With improvements in technology that make managing big data more accessible to the providers that need it, the medical profession has been able to see solutions to predict epidemics, cure disease, improve quality of life, and avoid preventable deaths. Better decisions can be made because of big data. Diseases and illnesses can be caught sooner so treatment options can begin quicker.
 IT doesn’t need to start with the medical professionals anymore. There are apps that patients can use to better understand and monitor their own health. The apps collect data that can be shared with providers for more data results over a longer period. The data is easier to share between providers and others evaluating it against baseline results. This helps to draw a more accurate and comprehensive conclusion about what is going on with a patient’s health.
IT doesn’t need to start with the medical professionals anymore. There are apps that patients can use to better understand and monitor their own health. The apps collect data that can be shared with providers for more data results over a longer period. The data is easier to share between providers and others evaluating it against baseline results. This helps to draw a more accurate and comprehensive conclusion about what is going on with a patient’s health.
Going further, big data provides comparisons between patients with similarities. It can be analyzed alongside thousands of others, highlighting specific threats and issues through patterns that emerge during the comparison. A provider can compare treatments and assess options based on results from other patients who deal with similar conditions. They can see the effects of prescriptions from patients with similar situations and risk factors like age, genetics, and lifestyle.
For a more in depth article on examples of how big data can transform the healthcare sector, read The big-data revolution in US health care: Accelerating value and innovation by McKinsey and Company.
 One of the biggest hurdles is overcoming the silos that typically prevent big data from being shared. While it is gathered in huge numbers, it is often kept in control of the different doctors, hospitals, clinics, and administrative departments. For years, even data within the same institution was kept within the specific department and not accessible to others. However, the medical industry has been starting to recognize the problems with these silos. They are starting to create data trails using technology to link together the information that connects to the different departments and providers. This helps everyone in the overall analysis.
One of the biggest hurdles is overcoming the silos that typically prevent big data from being shared. While it is gathered in huge numbers, it is often kept in control of the different doctors, hospitals, clinics, and administrative departments. For years, even data within the same institution was kept within the specific department and not accessible to others. However, the medical industry has been starting to recognize the problems with these silos. They are starting to create data trails using technology to link together the information that connects to the different departments and providers. This helps everyone in the overall analysis.
At Boost IT, we work with all different providers to maintain software that helps link data to multiple departments, associates, insurance companies, and others with appropriate authority so it can be shared to overcome the hurdles of silos and improve the overall health and well-being for everyone’s benefit.
Big Data in Clinical Trials
Just as big data can be used to help determine the best treatment options, it is also put back into the system for use in clinical trials. Huge amounts of data help the researchers see the patient type and characteristics that make the best candidates for their drugs.
One big breakthrough with technology and medicine is personalization – where medicines are tailored to a person’s genetic makeup – which results from comparisons alongside thousands of others. Another advancement is the use in technology to prevent epidemics by determining large areas potentially affected by disease.
A big hurdle in using big data for clinical trials is with privacy and security. Extreme security safeguards must be put in place to limit accessibility so only those authorized to see the data can access it. Threats like security breaches are continuous concerns.
Boost IT has over 20 years of experience and continuous training in IT security to protect and manage big data so it remains private and secure. We understand the risks and need for staying current on cybersecurity so we can help you have the best protection against cyber threats. For more information, contact us at 404-865-1289.


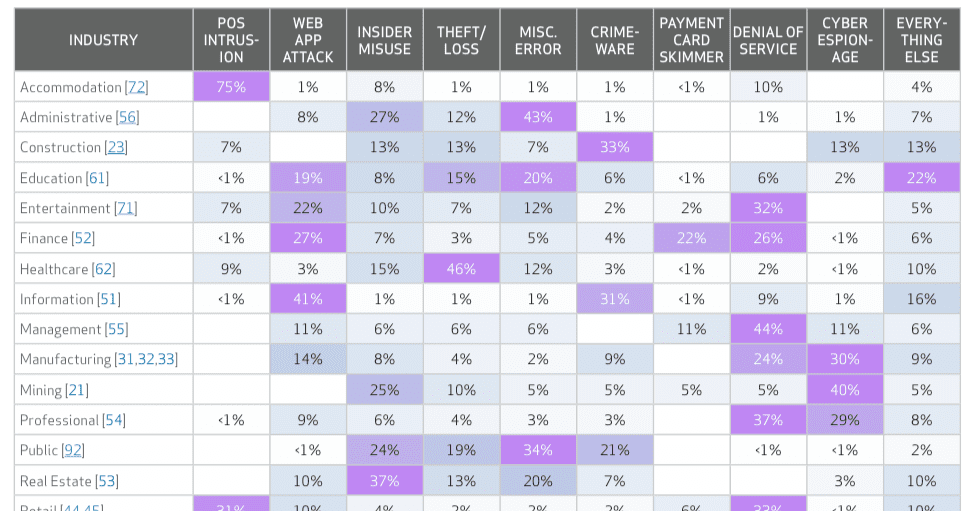
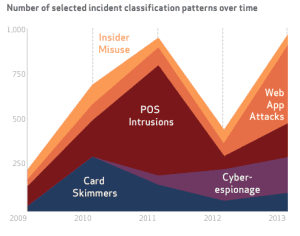

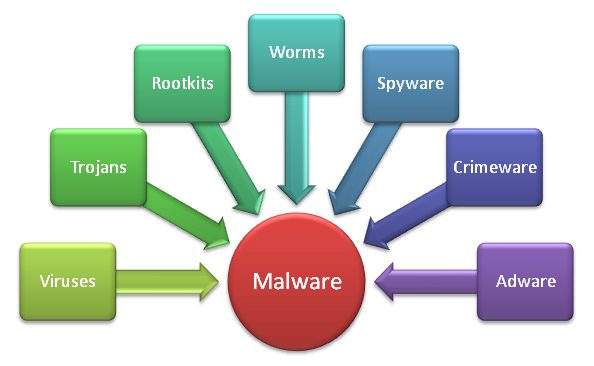
 Anthem was hacked because of the amount of data they have, but even if you don’t store SSNs, malware can cripple small and mid-sized businesses, too. So we wrote 4 blog posts over the past month with easy to implement cyber security tips. A great security strategy keeps tangible and intangible costs down, protects your clients, co-workers or patients, and provides the most reliable access to your data. Boost IT’s strategy has worked very well for the past 15 years. Not one of our clients has gotten infected with
Anthem was hacked because of the amount of data they have, but even if you don’t store SSNs, malware can cripple small and mid-sized businesses, too. So we wrote 4 blog posts over the past month with easy to implement cyber security tips. A great security strategy keeps tangible and intangible costs down, protects your clients, co-workers or patients, and provides the most reliable access to your data. Boost IT’s strategy has worked very well for the past 15 years. Not one of our clients has gotten infected with  We are starting to realize that a
We are starting to realize that a