Security Breach Report 2014
Breaches Doubled in 2014, Financial Losses up 34%

The security breach report showed that security breaches doubled in 2014, and are on the rise, and it is no surprise to find that as the number of information security incidents continues to mount, so do financial losses. The 2014 Verizon Data Breach Investigations Report (DBIR) shows the highest risk threat types by industry and specific steps to prevent those incident patterns.
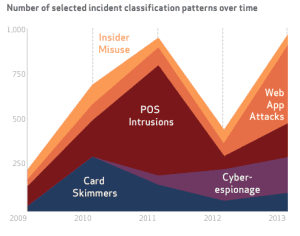
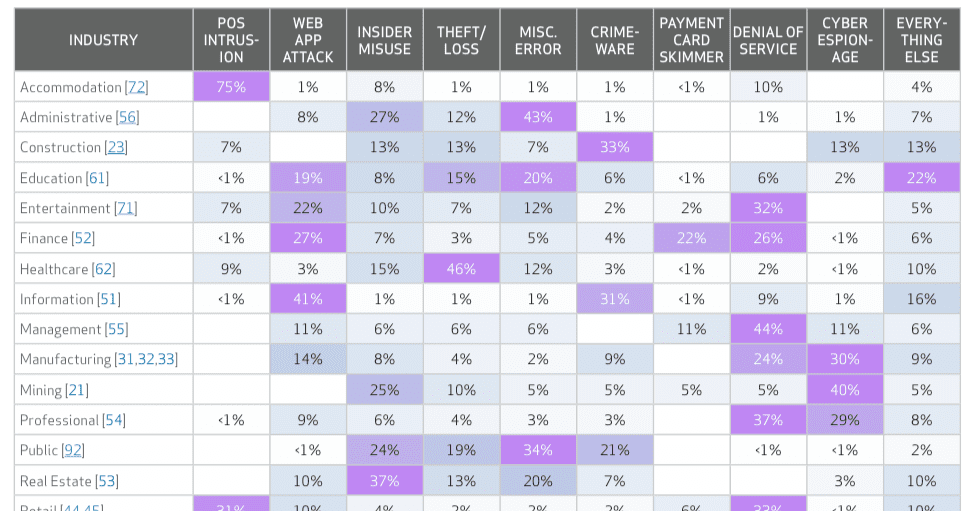
The highest number of security incidents were attributed to:
- Web App Attacks
- Insider Misuse
- Crimeware
- Denial-of-Service
- Cyber Espionage
- Theft/Loss
Finance, Retail, & Professional Services were some of the most targeted industries outside of the public & information sectors.
Security Adviser, Roger A. Grimes of InfoWorld, discussed 5 main takeaways from the Verizon report if you’d like a brief summary.

A recently released PwC Security breach report showed that the number of detected incidents soared to a total of 42.8 million, a 48% leap over 2013. This increase comes at a great cost:
- Total security-related financial losses increased by 34% over 2013.
- Cyber security risks will never be completely eliminated.
- Businesses must remain steadfast and agile considering there is a constantly changing security landscape.
Your company should consider implementing a 4-pronged approach to security to protect your valuable assets and proactively address the most common threats.
Based on some of Verizon’s recommended controls in this infographic, it confirms our thinking is on target. Apply these cyber security principles to small and mid-sized businesses. The full list is in the Verizon security breach report. Boost IT released 4 Cyber Security Tips for SMBs last month if you’d like to read more about how we can secure your data and protect your business.
