Boost IT provides Cryptolocker removal and prevention services in the Atlanta, GA area. Preventing Cryptolocker attacks and removing Cryptolocker helps secure your company’s files and assets.
How does Cryptolocker strike?
An end user opens an email attachment. Little do they know the attachment contains Cryptolocker. Once opened, Cryptolocker encrypts the victim’s files with multiple algorithms, making the encryption very difficult to break. Then it demands a ransom.
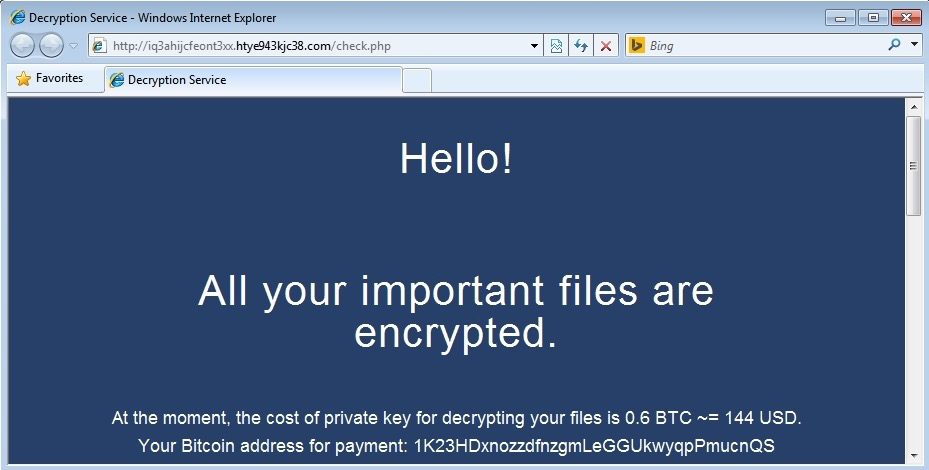
The ransom is tied to a deadline. When that deadline expires, the ransom doubles. But paying the ransom is no guarantee that the hacker will release the decryption key. In fact, it’s more common that they’ll just ask for more money to decrypt your files.
Cryptolocker is one of the most successful types of ransomware ever produced, with an estimated cost to organizations of over half a billion dollars.
Cryptolocker used to attack personal computers or individuals. Now hackers have started targeting businesses with this ransomware as well. Many organizations have found themselves facing significant financial losses not only from paying ransoms, but also fines for violating the Data Protection Act.
Attacked? Cryptolocker removal to the rescue!
We suggest you do not pay a ransom if you believe that your computer has been infected by Cryptolocker.
Boost IT’s threat engineers are Cryptolocker removal experts. We’ve also partnered with the best technology available to handle these threats. This technology, combined with our experience handling cyber security makes us specialists in cryptolocker removal and cryptolocker spread prevention.
We are ready for your call, email, or message.
Reach out to us today and tell us how we can help your organization succeed.
