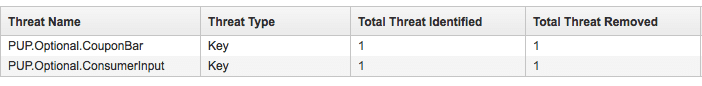
How Our Endpoint Protection Software Saved Payroll
Below is an e-mail we just sent to one of our clients.
The person we sent this e-mail to uses a computer that contains sensitive financial and personal data and is used for payroll. We are all very thankful for the endpoint protection software.
Suzanne,
Just wanted to keep you updated on our work and remind you that much of our security & protection work is done automatically without you even knowing about it.
Our endpoint protection software suite found a potentially unwanted program on your computer during a scan today. It was called ConsumerInput and was deleted automatically. Details of the program are at http://malwarefixes.com/threats/pup-optional-consumer-input/
In Feb 2013, the Federal Trade Commission approved a final order against the company that created the software, Compete Inc., for not protecting the data they collect. https://www.ftc.gov/news-events/press-releases/2013/02/ftc-approves-final-order-settling-charges-against-compete-inc.If you’ve updated or installed any software in the past couple days just be careful when installing it. If you were unaware that anything got installed I’m not surprised. Malware is getting sneakier.
Here’s an article on How to Prevent Malware BEFORE the Infection that shows you what to look for to prevent malware. It may help your family at home too.
https://www.boostitco.com/blog/how-to-recognize-malware-before-the-infection/
Our endpoint protection software suite is just one of the benefits of using a managed IT company instead of an IT guy/girl or an in-house part-time IT person where IT is not their primary job function.
In this case, our monitoring software alerted us about the issue and cleaned the computer automatically. Many other IT firms, even some of the big name IT firms, or IT pros don’t monitor your network at this level and even fewer automatically clean the computers.
Interested in this kind of protection for your business?
